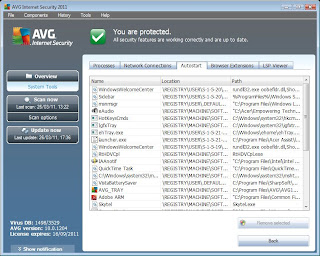
Is your Windows Task Manager, registry editor (regedit) and Microsoft Configuration setting (msconfig) being blocked by malware??? Don't worry AVG Internet Security 2011 got Component System Tools.
The System Tools component is an advanced tool for detailed system analysis, as to what is happening on your computer at the moment.
It lists (and allows you to terminate or delete) individual active processes and applications currently running on your computer, open network connections, installed browser plugins and LSPs, and applications that are launched automatically after Windows startup.
The following tabs are available in the component overview:
· Processes
The Processes tab can replace Windows Task Manager (ctrl+shift+esc) function, when this windows tool has been blocked by malware.
The Processes tab displays a list of processes (i.e. running applications) that are currently active. The list contains some of the following columns (depending upon whether the Identity Protection component is installed):
· Severity displays an icon indicating the severity level of infection, as determined by the Identity Protection component.
· Process name indicates the name of the running process.
· Process path indicates the physical path to the running process.
· Window indicates the application Window name, if applicable.
· PID (Process Identification Number) is a Windows internal process identifier that uniquely identifies the process.
You can select an application and terminate it by pressing the Terminate Process button.
Note : Do not terminate any applications or processes, especially system services, unless you are absolutely sure that they represent a real threat! By terminating applications deliberately, you could seriously destabilize your system.
· Network Connections
The Network Connections tab displays a list of currently active connections. The list contains the following columns:
· Application indicates the name of an application that is related to the connection.
· Protocol indicates the transmission protocol type that is used for the connection: TCP, the protocol used in conjunction with Internet Protocol (IP) to transmit information over the Internet, or UDP, an alternative to TCP protocol.
· Local Address indicates the IP address of the local computer and the port number that is being used.
· Remote Address indicates the IP address of the remote computer and the port number that it is being connected to. If possible, it will also look up the hostname of the remote computer.
· State indicates the most probable current state.
To list only external connections, simply select the Hide local connections checkbox. This will hide all local loopback or some system related local connections that are usually not a real threat.
Operating buttons are as follows:
Press Terminate Connection to terminate one or more connections; select one or more rows that are currently in the connected state and press this button.
Press Terminate Process to terminate one or more applications that are related to the connection; select one or more rows and press this button.
Note: Sometimes it is only possible to terminate applications that are currently connected.
Note : Do not terminate any applications or connections unless you are absolutely sure that they represent a real threat. By terminating these deliberately, you could seriously destabilize your system.
· Autostart
Oftenly malware try to disable Registry Editor (regedit) and Microsoft Condiguration Setting (msconfig) in order to prevent the user using them. The Autostart tab can replace Registry Editor (regedit) and Ms Configuration settings (msconfig), useful to remove registry value of startup application and also delete the startup application file directly.
The Autostart tab displays a list of all applications that are executed during Windows system start-up. The list contains the following columns:
· Name of the application
· Location in the Registry
· Path to the application (physical location on your disk)
Very often, several malware applications add themselves automatically to the start-up registry entry. You can delete one or more entries by selecting them and pressing the Remove selected button.
Note : Do not delete any applications from the list unless you are absolutely sure that they represent a real threat. If you are unsure, use the Internet and your favorite search engine to find more information about the application name.
· Browser Extensions
The Browser Extensions tab displays a list of plugins (applications) that are installed inside your Internet browser. The list may contain regular application plugins as well as potential malware programs. Click on the listed object to obtain more information. Plugins listed with a green icon are usually known and keeping them is quite safe. Please note however that certain malware programs can pretend to be something else, therefore it cannot be 100% guaranteed that any plugin is harmless.
After selecting an object from the list, its description appears in the bottom part of the tab. In the Technical Details section, CLSID represents a unique identification tag that is associated with an ActiveX or OLE 2.0 object created by a specific component or server. Clicking the CLSID link will open up your Internet browser and search for the string in the Google search engine. After obtaining more information on the plugin, you should be able to decide whether the object should be removed or not.
You can delete any entry in the list by selecting it and pressing the Remove selected object button.
Please note that any browser extension and relevant info might be listed, but only those of Internet Explorer can be guaranteed!
Note : Do not delete any plugins from the list unless you are sure that they represent a real threat. If you are unsure, use the Internet and your favorite search engine to find more information about the plugin name.
· LSP Viewer
The LSP Viewer tab displays a list of Layered Service Providers (LSP).
A Layered Service Provider (LSP) is a system driver linked into the networking services of the Windows operating system. It has access to all data entering and leaving the computer, including the ability to modify this data. Some LSPs are necessary to allow Windows to connect you to other computers, including the Internet. But certain malware applications may also install themselves as an LSP, thus having access to all data your computer transmits. Therefore this review may help you to check all possible LSP threats.
It is also sometimes possible to repair broken LSPs (for example when the file has been removed but the registry entries remained untouched). A new button for fixing the issue is displayed once a repairable LSP is discovered.
To exclude Windows LSPs (which are most likely harmless) from the list, check the Hide Windows LSP box.
This System Tools component only available on AVG Internet Security 2011 version, provides more protection and better performance than the other version.
Tough on threats
Easy on you
Enjov AVG
· Processes
The Processes tab can replace Windows Task Manager (ctrl+shift+esc) function, when this windows tool has been blocked by malware.
The Processes tab displays a list of processes (i.e. running applications) that are currently active. The list contains some of the following columns (depending upon whether the Identity Protection component is installed):
· Severity displays an icon indicating the severity level of infection, as determined by the Identity Protection component.
· Process name indicates the name of the running process.
· Process path indicates the physical path to the running process.
· Window indicates the application Window name, if applicable.
· PID (Process Identification Number) is a Windows internal process identifier that uniquely identifies the process.
You can select an application and terminate it by pressing the Terminate Process button.
Note : Do not terminate any applications or processes, especially system services, unless you are absolutely sure that they represent a real threat! By terminating applications deliberately, you could seriously destabilize your system.
· Network Connections
The Network Connections tab displays a list of currently active connections. The list contains the following columns:
· Application indicates the name of an application that is related to the connection.
· Protocol indicates the transmission protocol type that is used for the connection: TCP, the protocol used in conjunction with Internet Protocol (IP) to transmit information over the Internet, or UDP, an alternative to TCP protocol.
· Local Address indicates the IP address of the local computer and the port number that is being used.
· Remote Address indicates the IP address of the remote computer and the port number that it is being connected to. If possible, it will also look up the hostname of the remote computer.
· State indicates the most probable current state.
To list only external connections, simply select the Hide local connections checkbox. This will hide all local loopback or some system related local connections that are usually not a real threat.
Operating buttons are as follows:
Press Terminate Connection to terminate one or more connections; select one or more rows that are currently in the connected state and press this button.
Press Terminate Process to terminate one or more applications that are related to the connection; select one or more rows and press this button.
Note: Sometimes it is only possible to terminate applications that are currently connected.
Note : Do not terminate any applications or connections unless you are absolutely sure that they represent a real threat. By terminating these deliberately, you could seriously destabilize your system.
· Autostart
Oftenly malware try to disable Registry Editor (regedit) and Microsoft Condiguration Setting (msconfig) in order to prevent the user using them. The Autostart tab can replace Registry Editor (regedit) and Ms Configuration settings (msconfig), useful to remove registry value of startup application and also delete the startup application file directly.
The Autostart tab displays a list of all applications that are executed during Windows system start-up. The list contains the following columns:
· Name of the application
· Location in the Registry
· Path to the application (physical location on your disk)
Very often, several malware applications add themselves automatically to the start-up registry entry. You can delete one or more entries by selecting them and pressing the Remove selected button.
Note : Do not delete any applications from the list unless you are absolutely sure that they represent a real threat. If you are unsure, use the Internet and your favorite search engine to find more information about the application name.
· Browser Extensions
The Browser Extensions tab displays a list of plugins (applications) that are installed inside your Internet browser. The list may contain regular application plugins as well as potential malware programs. Click on the listed object to obtain more information. Plugins listed with a green icon are usually known and keeping them is quite safe. Please note however that certain malware programs can pretend to be something else, therefore it cannot be 100% guaranteed that any plugin is harmless.
After selecting an object from the list, its description appears in the bottom part of the tab. In the Technical Details section, CLSID represents a unique identification tag that is associated with an ActiveX or OLE 2.0 object created by a specific component or server. Clicking the CLSID link will open up your Internet browser and search for the string in the Google search engine. After obtaining more information on the plugin, you should be able to decide whether the object should be removed or not.
You can delete any entry in the list by selecting it and pressing the Remove selected object button.
Please note that any browser extension and relevant info might be listed, but only those of Internet Explorer can be guaranteed!
Note : Do not delete any plugins from the list unless you are sure that they represent a real threat. If you are unsure, use the Internet and your favorite search engine to find more information about the plugin name.
· LSP Viewer
The LSP Viewer tab displays a list of Layered Service Providers (LSP).
A Layered Service Provider (LSP) is a system driver linked into the networking services of the Windows operating system. It has access to all data entering and leaving the computer, including the ability to modify this data. Some LSPs are necessary to allow Windows to connect you to other computers, including the Internet. But certain malware applications may also install themselves as an LSP, thus having access to all data your computer transmits. Therefore this review may help you to check all possible LSP threats.
It is also sometimes possible to repair broken LSPs (for example when the file has been removed but the registry entries remained untouched). A new button for fixing the issue is displayed once a repairable LSP is discovered.
To exclude Windows LSPs (which are most likely harmless) from the list, check the Hide Windows LSP box.
This System Tools component only available on AVG Internet Security 2011 version, provides more protection and better performance than the other version.
Tough on threats
Easy on you
Enjov AVG